Unpatched iOS 9 Mobile Device Management Hack ‘SideStepper’ Wrecks Havoc on Enterprises
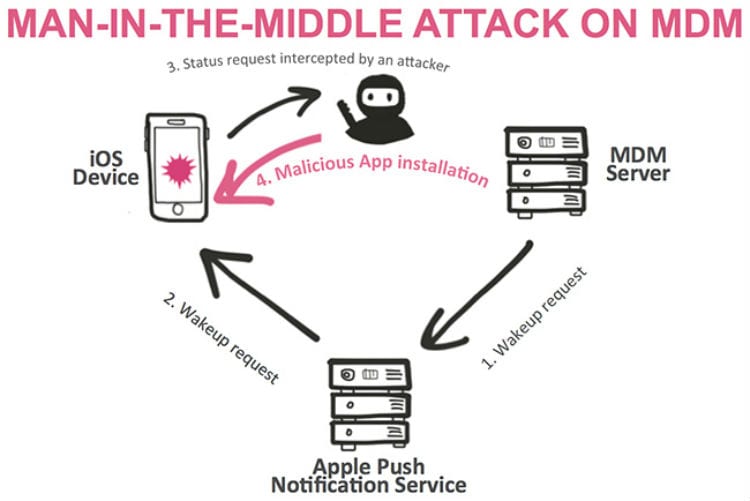
It has been found that the built in Mobile Device Management (MDM) implementation in iOS 9 is susceptible to man-in-the-middle attacks and can be used to install malware on iOS devices. This hack, SideStepper, is a phishing attack that targets employees and completely takes over the device. Hackers are sending legitimate looking SMS messages to prompt the download or update of familiar applications to gain remote access to the devices, effectively ‘side stepping’ the security features of iOS MDM.
In this relatively strange twist of events; the fact that enterprises often have employees download apps off of an enterprise app store as opposed to the Apple App Store. that could be the downfall. SideStepper releases pop ups indicating updates for typical mobile device management platforms that are opening the doors for total malicious control of the corporate devices. This only needs to happen to one device one time in order to effectually compromise all corporate data.

Image courtesy of www.helpnetsecurity.com
According to PCWorld, in a presentation at the Black Hat Asia security conference on Friday, researchers from Check Point Software Technologies demonstrated that the communication between MDM products and iOS devices is susceptible to man-in-the-middle attacks and can be hijacked to install malware on non-jailbroken devices with little user interaction.
“We found a way to do a man-in-the-middle attack on an iOS mobile device and replace an original command such as ‘query device’ with one to install a malicious enterprise certificate application,” says Ohad Bobrov of Check Point. “[It] pretty much seamlessly installs a malicious application on the device, and then game over.”
Hackers are stealing Enterprise Deployment certificates These are code-signing certificates obtained through the Apple Developer Enterprise Program that allow companies to distribute internal apps to iOS devices without publishing them in the public app store.
Older versions of iOS, in order to deploy and app the user had to obtain an enterprise certificate for that app, open a link where the app was hosted, agree to trust the developer, and the agree to install the app. In an effort to eliminate the obvious abuse of these implementation, Apple added additional steps to the deployment process. What they didn’t realize is that they updated everything else, but didn’t really change how enterprise apps are installed on devices.
What makes this threat so serious is that there really isn’t anything IT can do to detect it at the moment. The only real defense would be keeping a log of all updates and downloads that employees are making, or having IT screen and manage every individual user update. Both of these methods are tedious and not wholly effective.