How Secure Is Your IaaS? Compare The Top 5 CSP’s Security

In a new report, IaaS Security State of Industry, cloud security solutions provider FourtyCloud released the results of their yearly survey of major public IaaS cloud service providers (CSPs). What they found might surprise you.
For their report, FourtyClouds surveyed the security capabiliteis of the top five IaaS providers— Amazon Web Services (AWS), Google Cloud Platform (GCP), IBM Cloud, Rackspace, and Azure— with a specific focus on data and network security, as well as identity and access management (IAM).
FortyClouds notes that, while the cloud IaaS market continues to grow (Gartner predicts 38% growth in coming years), none of the leading CSP’s native public cloud offerings have shown strong advances in security in the past year. FortyClouds recommends that IaaS customers augment their IaaS solutions with third party security solutions.
[From AWS to Rackspace, Solutions Review rounds up the top 28 cloud vendors in the 2015 Cloud Platform Solutions Buyer’s Guide. Solutions Review Buyer’s Guides include full market overviews and 10 questions designed to help find your best fit in the cloud. Download your free copy today.]
FortyCloud’s research examines seven features of each CSP’s native security abilities, here’s how they’re defined in the blog post:
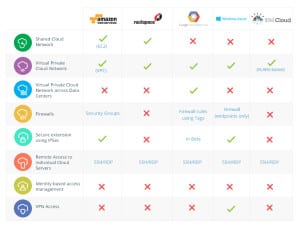
Shared Cloud Network: The public IaaS environment where cloud customers share a cloud service subnet. Each VM usually has a public IP address (permanent or temporary) as well as service IP address for the internal cloud service network.
Virtual Private Cloud (VPC) Network: The IaaS provider supports an isolation of customer’s cloud deployments, such that a customer can have a private subnet that is not reachable from other customers cloud servers or from the public internet.
Firewall: Collection of policies and rules to control the traffic allowed between a group of cloud servers or static IP addresses.
Identity-based access management (IAM): Firewall rules based on user identity that allow specific users to access specific sets of compute resources.
Secure extension:The ability to securely connect enterprise sites to the cloud deployment (usually a virtual private network) via static IPSec connections.
Secure remote access to individual servers:The ability to access an individual VM using a secure protocol (such as SSH or RDP); this type of remote access is usually based on credentials that are specific to a single user and a single server.
Remote VPN access: The ability of the organization’s employees to securely connect on demand to the cloud deployment remotely using VPN clients; this includes central authentication of the employee’s’ identity prior to gaining access to the cloud deployment (art of all of cloud servers).
FortyCloud calls the shared cloud network “the least secure public IaaS option,” noting that access to individual tenant’s compute resources could be obtained by others from within the cloud data center.
AWS EC2 Classic and Rackspace both provide shared cloud networks, though the former is currently transitioning to using VPCs as the default for new environments. The other three vendors evaluated do not offer shared cloud networks, instead they opt for more secure virtual private networks.
In the firewall category, AWS and GCP offer full firewall controls and configurations, while Azure offers endpoint only firewall capabilities. Rackspace and IBM do not offer any stock firewall capabilities.
Notably, none of the major IaaS CSPs offer native IAM solutions, though there are dozens of third party solutions available. Azure does provide dynamic client based VPN access to the cloud, but does not support identity based access.
FortyCloud adds that several CSPs do offer central-identity based access to service management consoles and APIs, but not to the cloud servers themselves.
FourtyCloud’s comparison only considered security features native to each public cloud IaaS offering. In many cases, missing security features can be supplemented with additional paid services available in each vendor’smarketplace.
Disclaimer:
It is important to note that although the completeness of security offering is an important attribute in selecting your cloud provider, other attributes like maturity, service coverage, and level of support are also important factors in such a decision. this post does not consider the later factors.
To view the results of FortyCloud’s research in their entirety, read their blog post here.
Widget not in any sidebars