CyberArk Provides Actionable Analytics for IAM to Prevent Cyber-Attacks
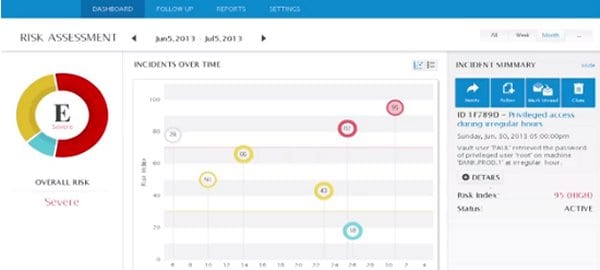
 In late 2013 CyberArk, a leader in securing enterprises against cyber-attacks, announced the availability of a new analytics solutions that detects malicious privileged account behavior. Privileged Threat Analytics from CyberArk is intended to disrupt in-progress attacks before damage is done to the business and is apparently the industry’s first solutions with such capabilities.
In late 2013 CyberArk, a leader in securing enterprises against cyber-attacks, announced the availability of a new analytics solutions that detects malicious privileged account behavior. Privileged Threat Analytics from CyberArk is intended to disrupt in-progress attacks before damage is done to the business and is apparently the industry’s first solutions with such capabilities.
Providing targeted and actionable analytics Privileged Threat Analytics allows IT to address what security consultancy firm Mandiant says is a primary target for internal and advanced external attacks. “APT intruders prefer to leverage privileged accounts where possible, such as domain administrators, service accounts with domain privileges, local administrator accounts, and privileged user accounts.”
The release of Privileged Threat Analytics helps to protect organizations against what CyberArk is calling the new “battleground” for security which they claim is now inside the network. Roy Adar, vice president of product management for CyberArk states that, ““Organizations must assume attackers have already penetrated the perimeter and once inside, will almost always attempt to take control of privileged accounts to advance their attack. Customers are asking for controls on privileged accounts, coupled with the ability to detect suspicious activity to protect their organizations from evolving threats.”
Here is a quick list of the benefits provided by Privileged Threat Analytics from CyberArk’s press release:
- Identifies in-progress external attacks and malicious behavior of authorized insiders;
- Detects a range of anomalies in the behavior patterns of individual privileged users in real-time, such as a user who suddenly accesses credentials at an unusual time of day. This is a strong indicator of malicious activity or severe policy violations such as password sharing;
- Improves effectiveness of SIEM systems and incident response teams by reducing false positives;
- Stops an in-progress attack earlier in the kill chain, ensuring a less costly and time consuming remediation process;
- Continuously learns user behavior and adjusts risk assessments based on the authorized privileged user activity patterns.
Click here to read the full release and to learn more about Privileged Threat Analytics.



















