It’s Time To Think Beyond IAM Solutions

As part of Solutions Review’s Premium Content Series—a collection of contributed columns written by industry experts in maturing software categories—Jim Barkdoll, the President and Chief Commercial Officer at Axiomatics, shares some expert insights on identity and access management (IAM), role-based access control (RBAC), and attribute-based access control (ABAC).
 Leading an enterprise IT team is no easy task. Global enterprises often have hundreds or even thousands of disparate applications, some of which are new, some legacy, and some based on unsupported software. Combined with a continuous increase in regulatory and security compliance requirements, dynamic aspects of burgeoning cloud applications, plus a ‘work from anywhere’ workforce, the result is challenging for even the most seasoned security experts.
Leading an enterprise IT team is no easy task. Global enterprises often have hundreds or even thousands of disparate applications, some of which are new, some legacy, and some based on unsupported software. Combined with a continuous increase in regulatory and security compliance requirements, dynamic aspects of burgeoning cloud applications, plus a ‘work from anywhere’ workforce, the result is challenging for even the most seasoned security experts.
Traditionally, organizations have turned to an identity and access management (IAM) solution to ensure workers get the access they need to do their jobs. Over the last decade, thanks in part to multiple compliance mandates and high-profile breaches, organizations shifted focus to ensure workers get only the access they need to only the data they need – nothing more.
This creates a balancing act for IT teams—the business requires access and speed to complete critical day-to-day activities, but they must also secure essential data and processes. Too much security and the business slows down. Too little and the organization might face financial and reputational damage via a costly public breach.
In the beginning, there was IAM.
In the last ten years, IAM solutions have matured and continue to save countless hours and avert headaches for today’s IT professionals. Additionally, these solutions have continued to evolve, offering enterprises faster and more sophisticated protection. This is particularly true when it comes to access, as without IAM, organizations would have to manage each applications’ or user’s access separately, which is neither manageable nor scalable.
Though this sounds ideal, the issue rises with the continuous stream of changes IT teams deal with daily. People leave and start new roles either within the organization or elsewhere; new compliance regulations are introduced, new applications and/or hardware are added, and so on. For years, role-based access control (RBAC) was used to address this. With RBAC, IT assigned a user to a role, and policies were established to state what each position could access and were often synched to a human resources system.
When a new user was hired, the IAM solution would assign them a role based on their job title. If their job title changed due to an internal transfer or they left the organization, the IAM system would capture this once it synched with the HR system, and the change would be made. Though this appears straightforward, it does not reflect a vital issue: context.
Context is everything, and without it, a security solution (including an IAM solution) misses the critical elements necessary to determine whether an access request should be granted or denied. This is particularly true when you consider social engineering, which is rapidly becoming the preferred method for attackers to access critical corporate assets. Through this method, if a bad actor tricks an employee into exposing their credentials, solely relying on an RBAC policy review might not prevent a breach, as illustrated by the scenario below.
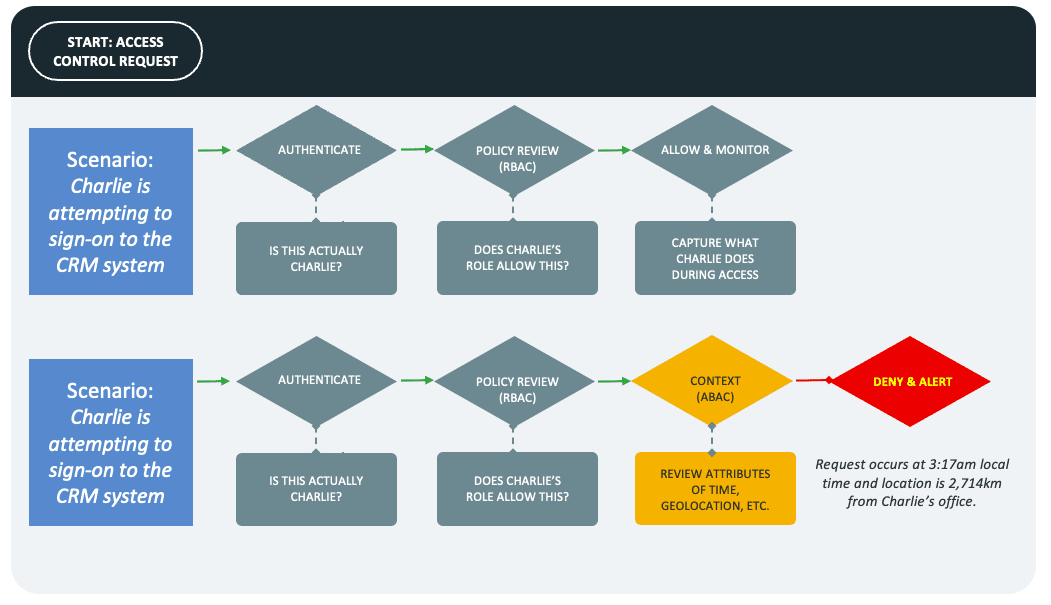
It’s time to address context.
Attribute-based access control (or ABAC) has been around for a while and was identified by the National Institute of Standards and Technology (NIST) as a critical component to eliminate risks from inappropriate access. In the NIST Special Publication 1800-3A: Attribute-Based Access Control, it was said, “Its [ABAC] dynamic capabilities offer greater efficiency, flexibility, scalability and security than traditional access control methods, without burdening administrators or users.” NIST first recommended ABAC adoption back in 2014.
More importantly, ABAC addresses safeguarding access to applications, databases, microservices, and APIs within a complex architecture, as seen in large, globally-matrixed enterprises. Instead of focusing on whether a role should permit access, ABAC considers attributes, including a user’s location, time of day, the device used, resource in question, or desired action. Reviewing attributes is done in real-time, which is why ABAC is well-suited to address the evolving challenges enterprises face.
Though IAM solutions promise a lot (and deliver on much), in many cases, they continue to contribute to a problem plaguing many enterprises’ role explosion. With RBAC, a reliance on roles can create a scenario where, for example, ten roles are made to address access, whereas one policy could handle the same situation through an ABAC-centric approach.
Implementing ABAC
The core of ABAC and the key to its implementation within an enterprise IAM environment lies in careful consideration of both enterprise attributes (discussed above) and policies. Leveraging ABAC, a user’s entitlements result from a runtime authorization request evaluated against a set of guidelines. This is a different approach to access and renders traditional access reviews ineffective. Successfully implementing ABAC in an enterprise IAM environment requires careful consideration of enterprise attributes and digital policies. ABAC requires new processes and new authorization requirements, which often leaves enterprise IT teams wondering where to begin.
A lifecycle policy is a systematic approach to implementing ABAC within the enterprise in eight steps, as seen below:
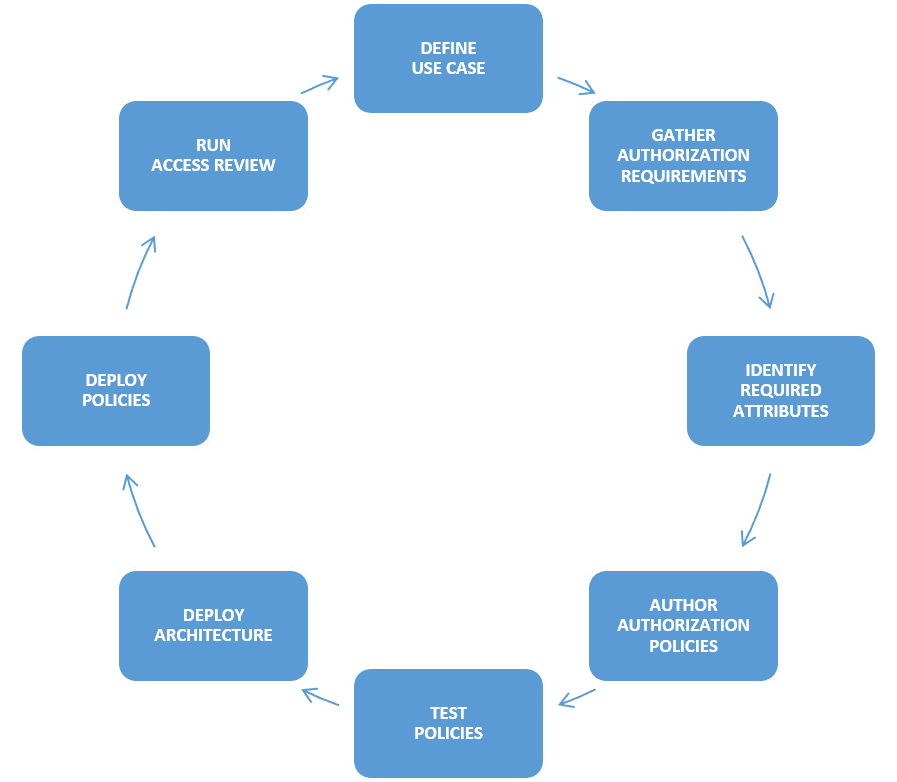
With new and evolving security and technology challenges emerging almost daily, traditional provisioning and de-provisioning are no longer sufficient. ABAC requires new processes and authorization requirements to be gathered but offers a modern approach to access management, moving away from the traditional, static approach entrenched in so many organizations. While IAM offerings have matured considerably in the last decade, what enterprises require has also evolved and requires a dynamic approach. Considering ABAC offers such an approach and a way for enterprises to ensure critical data and processes are only accessed by the right people, at the right time, in the right way.






















