Live from the 2018 Identiverse Conference in Boston, MA (Tuesday)


7:34 Good morning! Once again, Solutions Review is coming to you live from the Identiverse Conference at the Hynes Convention Center in Boston, MA! The Identiverse Conference is the largest event around digital identity in the world, and from what we’ve seen so far it’s been worth the wait! We’ll be once more updating throughout the day, giving you updates on the keynote sessions, break-out seminars, and key meetings with digital identity experts from around the country! Make sure to keep checking in!
7:56 We’re outside the Hynes Convention Center Ballroom, eagerly awaiting the opening keynote of the day: “The Unforeseen Forces Shaping Technology” presented by Andre Durand, Founder and CEO of Ping Identity and the Chair of the Identiverse Conference. This is sure to kick of a compelling day here!
8:01 Just let into the Ballroom!

8:12 Andre Durand of Ping Identity takes to stage to deliver the opening keynote of the day!
8:13 Andre Durand says that he is a firm believer of digital transformation. What will people be better at than machines in the future?
8:14 Keeping things simple will define winners and losers, according to Andre Durand.


8:16 Andre Durand talks about the “Mash Up” concerning the balance between security and convenience. There may not be a clear answer to this question. There needs to be a lot of granularity and fluid experiences.
8:17 Andre Durand speaks about his own observations of authentication and the changes to authentication he has seen.
8:19 Intelligence is the new frontier of value. This includes security and scalability. Breaches can take minutes but detection can take months. Humans can’t sift through this information fast enough to handle it.
8:20 AI can help us orchestrate identity into a central repository, according to Andre Durand.
8:21 APIs are eating software. Andre Durand of Ping Identity presents a graph showing the growth of public APIs and the contradictory high usage of private APIs.
8:23 Enterprises haven’t caught up with where future threats are going to come from. If APIs are the new way of access, how do we maintain visibility for security? How do protect our APIs from hackers or insider threats? We all have blind spots.
8:25 Andre Durand announces acquisition of machine learning, and AI for APIs vendor Elastic Beam. Andre Durand invites Bernard Harguindeguy, SVP Intelligence at Ping Identity onto the Keynote stage. Details to follow.

8:30 Bernard Harguindeguy, SVP Intelligence at Ping Identity, describes the new PingIntelligence for APIs solution.
8:32 The PingIntelligence for APIs seems capable of identifying stolen tokens and blocking access to tokens identified as stolen. The solution will be available in late Q3. Andre Durand retakes the stage.
8:33 We need to make identity smarter, says Mr. Durand. Identity cannot be an island. We need to build personal relationships at all levels even among competitors.
8:34 Andre Durand describes the Identity Defined Security Alliance, including Okta, LogRhythm, ThreatMetrix, and Optiv, among others. There are 17 vendors in all. It is meant to accelerate the integration of those technologies to achieve goals.
8:36 On the integration front, there is an enormous challenge and a lack of capacity to make all this stuff work faster. We’re all trying to make it easier, but environments are complicated. These technical partnerships are essential, none of the partners are treated as external.
8:39 Andre Durand describes the rise of global authentication authority, which he thinks is profound. It is meant to reduce authentication and directory sprawl, bringing order to messy internal systems which impedes the integration of new technologies and digital transformation.
8:42 A global authentication authority bridges all of the cloud services and legacy solutions, serving as a common point for the on-premises enterprise. It seems to be a clean identity foundation for enterprises.
8:43 Andre Durand invites to the Identiverse Conference stage the representatives of three major companies -Thor Essman (CEO of Versent), Melinda Buston (Program Director of Telstra), and Jared Meier (Product Manager of HP) – to discuss their identity deployments.

8:49 Ms. Buston described the fragmented customer experience that impact Telstra’s ability to strengthen their brand. The focus on customer experience changed the way they approached technology, as did listening to the features customers wanted.
8:53 Mr. Essman talks about the identity experience (IX) that integrates the customer and the IT team experiences.
8:54 Mr. Meier describes the branding of experiences in HP through identity technology. Ms. Buston discusses the streamlining of the customer experience and the consolidation of UI in their apps.
8:57 The panelists discuss taking their digital footprint out of the cloud and what it means to be “done” versus what it means to be truly finished via automation. The latter requires being able to solve common problems in identity such as pre-provisioning via machines. Your hands are no longer the best tool for solving identity problems.
9:00 The panelists recommend that you describe your identity vision in as much detail as possible. Keeping your enterprise enthused is essential, and you cannot over-explain your vision.
9:03 The Morning Keynote of the Identiverse Conference 2018 is concluded!
9:09 Hanging out with the Optimal IdM folks here at the Identiverse Conference 2018! Keep an eye out for the interview between Solutions Review CEO Doug Atkinson and Chief Product Evangelist Mark Foust!

9:14 Our first scheduled break-out session of the day will be “Microsoft Presents: Changing the Game with Machine Learning” presented by Maria Puertas Calvo, Senior Data Scientist at Microsoft.
9:17 Following up on the acquisition announcement made by Andre Durand of Ping Identity during his opening Keynote, Elastic Beam uses ML to defend against API-based cyberattacks. Elastic Beam founder and CEO Bernard
Harguindeguy, who also spoke this morning, joined Ping Identity as Senior Vice President of Intelligence. According to their press release, Ping Identity is now the first IAM company to offer an intelligent identity solution for APIs, and their solution is designed prevent future API exploits.
9:28 This breakout session will be about building machine learning systems to optimize Identity Security and Productivity, according to the subtitle of the presentation.

9:30 Maria Puertas Calvo describes the disconnect between marketing and technical experts on machine learning. Plenty of people think rules and heuristics perform better, that without labels they can’t supervise learning, etc. ML is generally hard to understand on the technical side.
9:35 Machine learning can combat phishing attacks, password spray (trying common passwords against known account lists, and breach replay (trying stolen passwords from other sites).
9:37 The smart ML systems can let good users go through smoothly while stopping bad actors in their tracks. It can do that by looking IP addresses, behaviors, authentications, password resets, etc. When the risk of the interaction is high, they can block access automatically. For the majority of users, they aren’t going to even encounter the program.
9:38 If you are trying to detect a bad actor, the bad actor will try to obfuscate their activities. They’re constantly innovating to conceal themselves. Training a machine learning system to learn from the latest attacks and develop a digital immune system for those new attacks.
9:41 How did Microsoft overcome the problems in machine learning, according to Maria Puertas Calvo? 4 ways. Number one is be a domain expert. Know your data, and know what is good and bad (or suspicious) logins and access when you see it. Your employees probably aren’t logging in from Russia at 3 am. You can transform this data into a model machine learning can use in its autonomous functions.
9:44 The second way is to build layered defenses. Start with the easy steps and build your machine learning on top of it. Layers can include prevention, detection, and mitigation/remediation. Machine learning built on top of it can stop the more advanced attackers and reduce false positives from more rudimentary systems.
9:46 The third way is to invest in labels. Labels tell your machine learning what it should be looking for in threats. Without it, your machine learning is hampered. You need labels to train supervised ML models and to measure the model’s quality. Labels can be end user generated via built feedback loops, expert generated, or auto-generated.
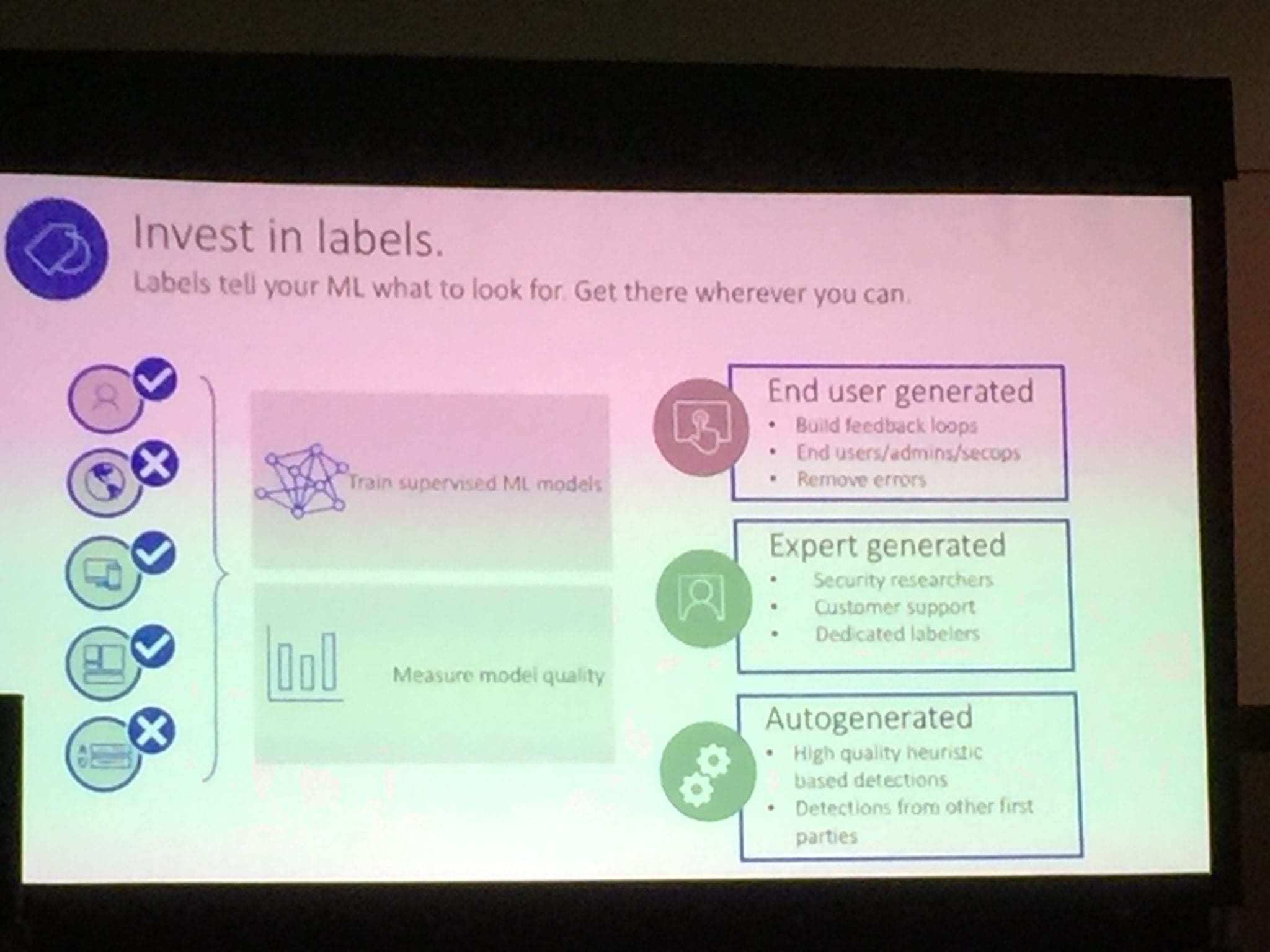
9:49 Lastly, know your numbers. You need to know where you need to invest. Measure the performance of all your detections. Machine learning can cause false positives and false negatives in all models. Therefore you need to determine how much friction you and your customers and employees are willing to endure to stop X% of threats.
9:53 Maria Puertas Calvo wraps up her break-out session on machine learning and identity at the 2018 Identiverse Conference!
9:59 Next up on the Identiverse Conference schedule is “IDMWORKS Presents: How To Make Your IAM Program A Success – Lessons Learned From The Field” presented by Paul Bedi, CEO of IDMWORKS. Incidentally, IDMWORKS has a sumo wrestler as part of their entourage. And they say identity professionals never have any fun.

10:06 This seminar is about IAM deployment. The first piece of advice: Clearly define the problem you are facing. Successful IAM programs start by defining the problem, not the solution. If you don’t understand the problem, you don’t know what you really need to solve it.
Widget not in any sidebars
10:07 The next lesson is to determine the true current state of your IAM before you deploy. You need to be truly accurate about where you are now (this does tie into the above advice). You can and will be held back by a lack of real knowledge of how your current system works and by the fear of change itself in your enterprise. Knowing how you do things now and why will result in fewer delays and a greater chance of success.
10:10 Next, documentation, documentation, documentation. Enterprises often have poor documentation of their own IT environments their processes. And how can you expect to effectively communicate information without documentation? Think about buying a new car: without documentation, how will you know when to get an oil change or when to take it to maintenance for proper upkeep? A lack of technical and procedural knowledge creates roadblocks to successful deployment.
10:12 When defining your problem, determine whether the problem is people, process, or technology.
10:13 Once you have accomplished all this, develop good requirements. Good IAM is designed as a solution to a business need, not just a technological need. Requirements need to be a joint determination by the business and technology sides of your enterprises. Without it, it can lead to scope creep.
10:14 Define the measure of success, according to Paul Bedi of IDMWorks at the Identiverse Conference 2018. Once you have requirements, you can measure success. How will your project be initiated and closed? Success will mean different things to different people in your enterprise. How will you communicate success then? Set benchmarks to demonstrate incremental wins, and define an end goal.
10:17 Once you begin deployment, identify and address internal politics issues early on. Make sure the stakeholders in the project are engaged. Don’t let internal tensions or bureaucracy disputes freeze your deployment. Resolve these problems early, and define procedures early on or beforehand. If individuals refuse to meet or answer questions, everyone is left guessing.
10:19 Remember the golden rule: data is everywhere. Data access governance tools have existed for a long time, but enterprises assumed they knew where their data was located. Yet IDMWORKS is finally starting to see enterprises waking up to the severity of the issue. Orphaned accounts can prove a nightmare, as can cloud migration and legacy solutions. Sensitive data often gets sent over emails.
10:21 Garbage going in will result in garbage going out. Poor quality and inconsistent data is pervasive.
10:22 IAM governance increases oversight. Identity governance is vital for controlling who has access to data and applications. Identity governance oversees IAM processes, creates and maintains IAM standards and policies, and prioritizes the enterprises’ IAM tasks and goals.
10:24 Impose best practice security measures on your engineers and developers. Have formal procedures for identity security that your employees are expected follow. Otherwise there is no accountability. You need to have some real strict policies and some real enforcement to back it up. Having four groups with four ways of handling data is going to create communications as well as unauthorized accesses.
10:26 Get the right people in the room, including the business people. IAM spans the enterprise, and it impacts disparate groups, including the business side. Just having IT in the conversation will result in time lost tracking down resources and confusion later on in the process.
10:28 Open communication is vital to project success. Communication is the key to good business regardless of industry. If your employees don’t understand what you are telling them, you have a problem. Make sure the communication is clear, summarized when necessary.
10:29 Communicate your changes in technology and processes. This ties into the same point above. Make sure you communicate changes BEFORE they happen. Sorry for shouting, it’s important.
10:30 IAM projects are continuous, not a one time project. Technology changes every 36 months. IAM needs to expand as your enterprise matures, and it needs to adapt to new technologies.
10:32 Paul Bedi concludes his break-away session at the Identiverse Conference 2018!
10:34 Next up at the Identiverse Conference, “Ping Identity Presents: Going Beyond SSO to Global Authentication Authority” presented by Eric Fazendin, Sr. Product Manager at Ping Identity.

10:39 Eric Fazendin of Ping Identity begins his breakaway session on SSO. Authentication authority is under internal and external pressures like mobile apps and IoT as well as messy internal systems.
10:41 Users of all types need access to all different sorts of apps and databases, and the need for centralization logins has never been higher. What is authentication authority? Enterprise-wide orchestration of access of any use case, access to APIs, and access for customers, partners, and employees.
10:43 Authentication authority provides better security. Authentication authority has four components: authentication sources, authentication policies, authentication sessions, and local identity profiles.
10:45 Authentication sources can include IdP adapters like HTML forms or Kerberos and IdP connections. IdP adapters challenge users for credentials, validates existing sessions, etc. IdP connections initiates authentication for 3rd party IdPs.
10:49 Authentication Policies builds on authentication sources. You can authenticate users via policies. Processing will branch throughout policies.
10:52 Authentication seems to be the name of the game today at the 2018 Identiverse Conference, as we can see in this presentation by Eric Fazendin of Ping Identity. Authentication policies are branching, multifaceted things that need to be adaptive to allow for smooth logins for the end-users while maintaining proper security of assets and databases. Granularity might be the word of the day – there is no “one-size-fits-all” authentication policy. You authentication policies need to adapt to factors such as the employee logging in, their role in your enterprise, the database or asset they wish to access, and the level of suspicion they generate (“why is Steve logging in from Turkey at 4 am?” as just an example).
10:57 Eric Fazendin of Ping Identity talks about the inevitable changes to identity that will happen, such as name changes, that will require self-service to reduce the burden on your IT help desks.
10:59 Eric Fazendin wraps up his breakout session on SSO with a Q&A.
11:03 As we wait for the next breakout session – “How Hearst Media’s modern IAM strategy improved security and helped set the pace for business” presented by Chris Suozzi, Executive Director, AD/Messaging and Identity Management at Hearst – a thought occurs to us. Much of the Identiverse Conference thus far has focused on identity and access management as both a technology problem and as a business problem. Our usual focus on this site – cybersecurity – has taken something of a backseat as it is considered another part of business processes and business efficiency.
Therefore, in the digital realm, identity might be considered the ultimate human problem, and its management the ultimate human solution as businesses and customer lifestyles continue to digitally transform. Perhaps nowhere was this theme more evident than at the beginning of the day, when Andre Durand’s keynote was preceded by a projected image of eyes opening.

11:13 The break-out session is about to start!
11:14 Chris Suozzi of Hearst explains Hearst’s business and its business demands as a media conglomerate. Challenges include security, especially for highly mobile users and access to corporate applications, Single Sign-On, reduction of multiple usernames and passwords on 3rd party applications, onboarding and offboarding, and cloud migration.
11:21 Other challenges include cost savings and the need for a consistent framework for simplified integration of in house applications. When Hearst began their journey, they had 50 AD forests, and they now have 5. Their digital infrastructure included a large number of SaaS applications, hundreds of email domain suffixes, a mixed device environment. and active directory migrations due to acquisitions.
11:25 Hearst recommends a phased approach to IAM deployment, similar to their own approach. Their first phase was the enablement of Office365. Afterwards they were able to leverage MFA, decommission on-premise exchange servers, and enablement of self-service password resets.
11:28 Heart’s second phase was to introduce the idea of single user name and passwords for 3rd party enterprise applications, and shut down Novell Access Manager. This all falls under the heading of true federation SSO. Hearst saw benefits as diverse as a more secure IT environment, ease of administration in cloud portals, and the use of the cloud as a control plane for MFA and conditional access.
11:34 Phase 3 for Hearst was to facilitate the on-boarding of identities to on-premise Active Directory from an Human Capital Management system. They saw benefits such as provisioning staff, consistent attribute values across the enterprise, and identity lifecycles driven by HR processes.
11:38 What is next for Hearst? Removal of ADFS to simplify the IT environment further and continued cloud migration.

11:40 What did Hearst learn in this identity journey? To understand the goals and issues of your enterprise you are trying to solve to properly plan and implement the features that best fit your enterprise’s goals. There are variations in implementations from vendor to vendor.
11:43 Chris Suozzi of Hearst is wrapping up his break-out sessions. We’re about to go to lunch before the big afternoon keynotes of the 2018 Identiverse Conference, but we’ll keep you updated with any meeting with cool vendors we have!

11:57 While at lunch we met Clare Nelson, CISSP, CIPP/E and CEO of ClearMark Consulting. She was a presenter here at the Identiverse Conference, and she gave us a little taste of her lecture on zero-knowledge proofs:
CN: Let’s say you wanted to read the news online. You can enter your subscription and they can give you personalized information: local weather for your area, horoscopes based on your birthday, etc. it’s not privacy perserving.
CN: With a zero-knowledge proof, you can instead say “I have a subscription,” and that would be the only statement on your identity the newspaper website obtains. With zero-knowledge proofs, you can make a statement that is authenticated as valid without giving anything else away. It’s privacy preserving, and can allow enterprises to be GDPR compliant automatically. It’s adoption is starting to ramp up, and since last month there are now standards for zero-knowledge proofs.
CN: Zero-knowledge proofs have been in PCs in TPMs for quite some time. These things are evolving. It could even make an American GDPR regulation easier to arise.
Thanks to Clare Nelson of ClearMark Consulting for her time and expertise!
12:40 We’ve been speaking to quite a few vendors here about the Idenitverse. A common theme has been that RSA, the largest cybersecurity conference in the world, might have become too big and that conferences like Identiverse are necessary to focusing in on identity issues and facilitating a community of identity vendors.
12:50 We just spoke to representatives from identity governance vendor Saviynt, who reported that there is an equal number of individuals interested in authentication and governance this year at the Identiverse Conference 2018.
12:52 We just spoke to representatives of zero-trust solution provider Centrify, who noted that identity has come a long way since the early days, and that complaints about cost and complexity are largely only accurate for legacy identity solutions.
1:06 We’re back in the Ballroom, awaiting the Identiverse Conference Afternoon Keynotes: “The Privacy Conundrum: Rights or Rewards?” by Jonathan Zittrain (George Bemis Professor of International Law at Harvard Law School) and “The Insecurity of Things: Identity to the Rescue!” by Ken Munro (Partner & Founder of Pen Test Partners LLP).
1:21 The Keynotes are starting! Andrew Hindle, Content Chair of the Identiverse Conference, takes the stage! He is introducing Jonathan Zittrain to the stage!
1:23 Jonathan Zittrain notes the unease surrounding privacy in the identity field, especially when it comes to governmental regulations like GDPR.
1:24 Jonathan Zittrain also notes the Data Retention Directive, which speaks to a contradiction in identity: we feel like our information is too widespread as is, and yet we can;t get the information on bad actors we need.
1:26 Jonathan Zittrain discusses the questions of identity and the inherent issues of the internet when it comes to identity. The Internet was built on a fundamental trust that may be called misplaced when it comes to honesty with identity.

1:27 He speaks about key signing parties, in which people would gather to verify each other’s identities, which were big in the 90’s. He calls this distributed declared identity. A vestige of a past era? Not truly. Think of your connections on LinkedIn. If the individual and you have 27 mutual friends, you will trust their link request far more.
1:29 You can also “fill in the blanks” via social media and derive an identity by looking at what a user likes or does online. This may be termed an derived identity.
1:31 Yet no one is taking responsibility of derived identities. Jonathan Zittrain mentions a study that shows Facebook could predict romantic partnerships before they happen. Other studies found social media could predict other things like marriages, graduations, or death (the users’ or people associated with the users’). And they use this information to direct market.
1:33 Artificial intelligence is contributing to this phenomenon in a way that is provoking anxiety from tech experts from around the world.
1:36 Jonathan Zittrain discusses the power of social media to affect voter behaviors and ultimately their political behaviors, and how individuals’ identities can be targeted via derived identities to accept fake news. The concept is called “micro-targeting.”
1:39 Micro-targeting can find correlations where you might think none exist. It has economic implications as well.
1:40 There is a legal intervention that Jonathan Zittrain and colleagues have been mulling over on digital identity called fiduciary duty, similar to the duty a doctor has to a patient or a lawyer to a client. The law recognizes a special duty of loyalty that when you share secrets with these individuals they are legally obligated to keep them. It also means they are obligated to help you or at least not to cause you direct harm by their actions.
1:42 For example, the top four hits on “should I vaccinate my child?” on Google say “no.” What obligation does Google have to give accurate information or to promote accurate information?
1:44 The answer may not be binary. Think about law enforcement. A fiduciary duty would mean asking for a warrant before letting law enforcement use a Google assistant as a microphone.
1:46 Google Image Search can be fooled into thinking that a picture of a cat is a picture of guacamole via a single pixel change. It speaks continual problems with AI that have broader implications like for self-driving cars.
1:49 But the idea here is that these small tweaks, invisible to the human eye, prevents derived identity collection methods (or renders them comical rather than insidious). Should we be facilitating this?
1:50 It may be time for the learned profession of the data scientist.
1:52 We, as technology experts, have an obligation to answer these questions to the best of our abilities for those to whom information technology is magic. We need to be part of the conversation actively.
1:53 Jonathan Zittrain concludes his keynote!
1:55 Andrew Hindle introduces Ken Munro to the Identiverse Conference stage!
1:55 Ken Munro talks about his discovery of the security issues of the IoT including the Samsung TV listening discovery.
1:56 Ken Munro talks about the Wi-Fi enabled kettle, common in Europe. He decided to see how easily he could hack one.

1:58 He was able to find a default manufacturer password on his first try. IoT is like going back in time to far less secure age.
1:59 He started looking at the app connected to the kettle and started to figure out how the two communicated.
2:00 From all this, Ken Munro was able to find the Wi-Fi encryption key. Really. with the right tools, you can basically buy people’s wi-fi encryption keys with little more than a kettle. Yet when Ken Munro tried to bring this fact to the manufacturer, he got the brush off. They eventually did make a better and more secure kettle, but it took years.
2:03 He also found an “internet-safe,” “non-profanity” interactive doll with cell phone and internet connections built in. His question? “Can I make you swear?” (The answer is yes).
2:05 The doll will connect to basically any bluetooth device, and can be turned into a bug through it’s always on microphone, as Ken discovered. Ken Munro reverse engineered it, found the database that contained all the swear words the dool couldn’t say. Then he deleted it, which proved his point.
2:07 What makes Ken cross is that security isn’t difficult if you care about it. Ken has interacted with vendors that do care and do fix bugs quickly. But he also met a lot of IoT vendors who didn’t.
2:09 Another IoT security issue is revoking access, which is isn’t as common as it needs to be. And the implications of security breaches for IoT are very real. The My CloudPet scandal proves that. Ken found you can hack a smart fridge and get users’ email passwords.
2:13 Ransom and IoT has been talked about but never seen. Ken Munro decided to do a proof of concept to see if it was possible. The target was a heating system. Could someone hold heat for ransom?
2:14 He found the firmware online, easily turned the binary into a filesystem, and found that arbitrary commands could be executed because there was no verification. IoT developers keep believing that no one will never see the firmware ever again, and seem to forget that hackers exist. Ultimately, the answer was yes: the heating system could be held for ransom.
2:17 Now the question becomes can IoT be weaponized? With the right timing, IoT could be triggered to initiate mass blackouts. Ken Munro believes that poor IoT objects should be banned, that we as consumers shouldn’t be allowed to buy products this insecure. Some of the items he demonstrates have been banned in countries around the world.
2:20 Ken Munro says there needs to be regulation, legislation, and litigation, with an emphasis on the latter.
2:21 Andrew Hindle thanks Ken Munro once again for coming in and giving such an amazing Keynote!
2:27 This concludes our live coverage of the 2018 Identiverse Conference! We hope you enjoyed and can attend and see it with your own eyes next year! To see more on the Identiverse Conference, check out our Monday coverage here.
Be Sure to Check Out Our Other Resources:
How IAM Solves Onboarding and Offboarding Challenges
The Importance of Edge Use Access (With Identity Automation)
IAM vs CIAM: What’s the Difference?
The Role of Identity in Digital Transformation
The Current State of Biometric Authentication in IAM
Comparing the Top Identity and Access Management Solutions
Widget not in any sidebars

























