Old Threats, New Access: The Danger of Old Vulnerabilities


Solutions Review’s Expert Insights Series is a collection of contributed articles written by industry experts in enterprise software categories. Bud Broomhead of Viakoo warns that old vulnerabilities, left unchecked, can leave open doors to cyber-criminals.
 Zero-day vulnerabilities are dangerous. Unknown to cybersecurity teams by definition, they represent an opportunity for attackers to infiltrate networks through a door no one else knows exists. However, despite the attention zero days get among the security community and in the press, they are not the vulnerabilities most likely to come back to bite security teams. That distinction belongs to existing, unpatched vulnerabilities. According to Qualys, of the top five common vulnerabilities and exposures (CVEs) exploited for ransomware attacks over the last five years, more than 60 percent had a patch available since at least 2013.
Zero-day vulnerabilities are dangerous. Unknown to cybersecurity teams by definition, they represent an opportunity for attackers to infiltrate networks through a door no one else knows exists. However, despite the attention zero days get among the security community and in the press, they are not the vulnerabilities most likely to come back to bite security teams. That distinction belongs to existing, unpatched vulnerabilities. According to Qualys, of the top five common vulnerabilities and exposures (CVEs) exploited for ransomware attacks over the last five years, more than 60 percent had a patch available since at least 2013.
Here’s an even more alarming example: On Jan 25, 2023, Palo Alto Network’s Unit 42 research group revealed that between August and October 2022, 40 percent of all cyber incidents they tracked were from a single vulnerability in devices using RealTek chipsets. That single vulnerability is present in hundreds of devices and, at the time of writing this article, is still actively being exploited and likely will be for years to come because infected devices are still flowing through the supply chain, ready to be exploited as soon as they are put into service.
The questions naturally arise: what’s behind this trend, and how do we combat it?
To be even more specific, IoT/OT systems are the largest attack surface formed out of older vulnerabilities. These systems often contain multiple makes and models of devices (think IP cameras or sensors), which requires each manufacturer to make and distribute patches. In some cases, IoT/OT devices are used past their end-of-service dates (if it is still running, there is little motivation to spend money to replace them), meaning a patch will never be available. Further compounding the problem is that IoT/OT devices and applications are managed by the line of business and not the IT organization, creating a skill and knowledge gap when it comes to maintaining cyber hygiene.
Vulnerabilities: Patching Off New Access from Old Threats
The first dynamic to understand is that patching vulnerabilities is already an uphill battle for IoT/OT security teams; unlike traditional IT systems that have had automated patch management solutions for many years, the use of automated methods in IoT/OT is relatively new. Enterprise IoT/OT networks have grown in size and complexity by orders of magnitude over the last several years, incorporating disparate SaaS programs, unique blends of private and public cloud usage, an unpredictable mix of managed and unmanaged devices, remote workers accessing data from around the world, and more. The larger the network, the more potential weak points it hosts. Simply put, vulnerabilities are increasing faster than the people who manage them can patch, and teams need to focus on those they know to be commonly exploited. At the same time, attackers also understand this dynamic, actively looking for vulnerabilities that may have been deprioritized in triage. Numbers are on their side here: the NIST vulnerability database shows over 170,000 known vulnerabilities have accumulated in total, more than half with a critical or high severity. So while blue teams are applying patches to the latest and most technically severe exploits, attackers are scanning the CVE threat catalog to turn old threats into new access.
So what can security teams do to develop a strong cybersecurity posture for their organizations against an avalanche of threats? Two keys are prioritization and automation.
Prioritization
Threat severity scores are not universally applicable. These scores are designed to “capture the principal characteristics of a vulnerability and produce a numerical score reflecting its severity,” in the case of the Common Vulnerability Scoring System (CVSS), one of the industry standards. This severity is based on its potential exploitability, rather than its ability to do damage to a specific organization’s business operations. A vulnerability might be technically severe, but in the context of a particular organization, it may not offer access to any operationally important systems. At the same time, that organization might have a sprawling IoT/OT network of sensors and smart devices delivering critical data for the business. These networks are often neglected by security teams for a variety of reasons, but as an operationally important part of the business, any potential exploit in this vector must be prioritized compared to a vulnerability that is technically more “severe” but remains isolated from operations and sensitive data.
Automation
Of course, simply prioritizing better is insufficient to deal with the deluge of threats that plague the modern IoT/OT environment. The scale is too great, and moreover, the threat landscape is constantly changing. New threats emerge, old threats reemerge, and compliance standards change, not to mention a host of other parallel dynamics. As cloud usage expands, this complexity will only grow more challenging. Organizations must deploy automation to act as a force multiplier for their security teams. Automation can be used to discover, prioritize, and remediate vulnerabilities; the key is to calibrate that automation to best serve your security team’s goals and complement your organization’s own IT environment. A prime example of this is managing IoT networks.
Traditional tools for patch management typically don’t work on IoT devices. These devices can’t run agents, are widely distributed, and the update mechanisms vary from manufacturer to manufacturer and even from device model to model. Often, they require manual updates on site, and fall under the purview of operational security teams rather than IT security teams. In other words, remotely managing these networks can be next to impossible to do in a comprehensive manner without deploying automation. By leveraging a solution designed to be agentless, automated, and scalable, security teams are able to discover and manage an entire threat vector that was logistically inaccessible before.
Another reason to focus on automation is that IoT/OT systems have a strong dependency between the devices and the applications managing them. In the case of an application like a Video Management System (VMS), it must support not just the device but the firmware as well. This leads to an “arbitration” issue, where simply updating the device firmware to the latest version can wreck the entire workflow and functionality if the application does not support it. Therefore, automation is required to ensure that compatibility is maintained between the device firmware and the application.
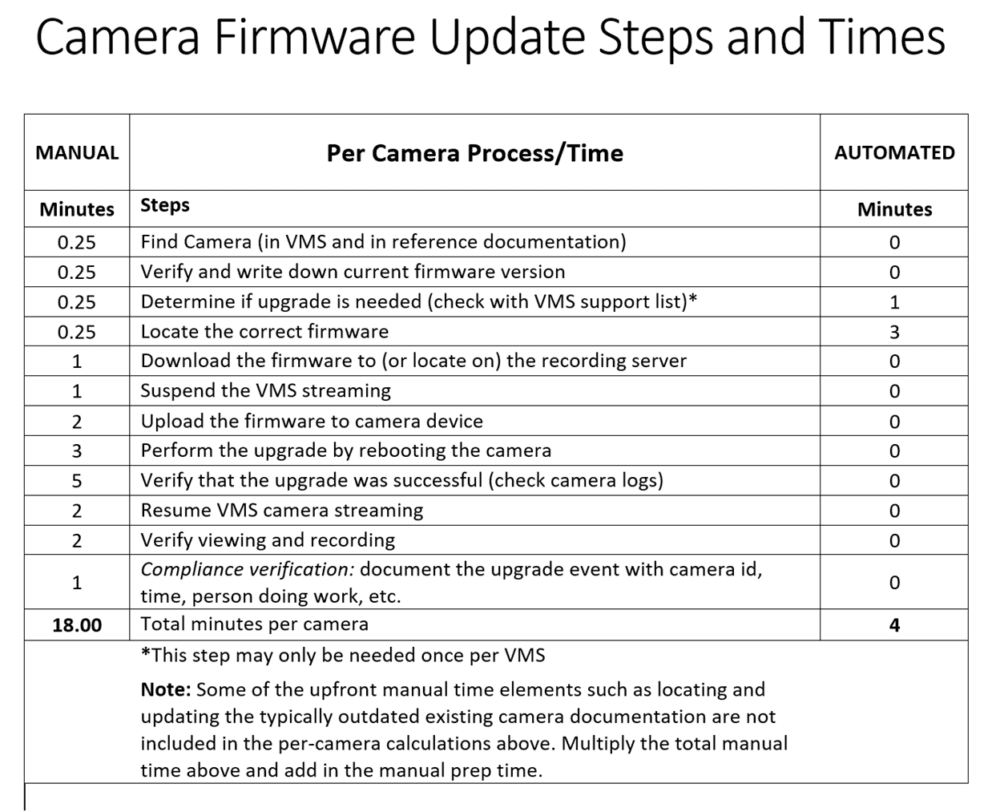
Noted security consultant Ray Bernard recently compiled a comparison of what it takes to perform firmware manually versus using automation; automation being 4.5X faster than manual methods. He also calculated the overall cost to the organization to be more than 6X less expensive using automation. Not considered in his analysis was the reality of whether an organization actually has the people to perform this work; in assessing one company with 8800 IoT/OT devices to be upgraded, he determined it would take 86 full-time personnel to do it.
Conclusion
Digital transformation is underway and accelerating with no end in sight. The massive changes that have rocked the business world – including the shift to hybrid work, notably – have expanded the enterprise attack surface far beyond what it has been in the past and into more invisible parts of the organizations, such as where IoT/OT devices operate. It is crucial to remember that the same advance in technology that serves digital transformation also benefits malicious actors. Therefore, security teams must adapt their practices and tools not only to fit the modern environment, but to be flexible enough to contend with the changes on the horizon. This requires a combination of organizational and technical efforts to be effective. Organizations should conduct thorough IOT/OT audits to identify the areas key to business operations and prioritize those for remediation. Teams must be empowered to defend these assets comprehensively, but they also need the tools to do so, meaning powerful automated tools that are able to confront the scale and complexity of cloud environments. While new threats might grab headlines, it’s the old threats that creep up and bite. By developing business-focused prioritization policies and implementing powerful automation to support the security team, organizations can put themselves in a strong position to defend against threats both old and new.





















