What’s Changed: Gartner 2017 Magic Quadrant for Identity Governance and Administration (IGA)

(Editor’s Note: Gartner released its 2018 iteration of the Gartner Magic Quadrant for Identity Governance and Administration, which you can read here. We’ve left this article up as part of historical preservation efforts—it is just as important to understand how cybersecurity technology has evolved as to understand where it is now. Furthermore, we believe that many of the best practices in this article are just as relevant today as they were the year prior.)
Analyst house Gartner, Inc. has released the latest iteration of its annual Identity Governance and Administration (IGA) Magic Quadrant (MQ) report.
In the Gartner 2017 Magic Quadrant for IGA,, Gartner evaluates the strengths and weaknesses of 13 vendors that it considers most significant in the IGA market, and provides readers with a graph (the Magic Quadrant) plotting the vendors based on their ability to execute and their completeness of vision. The graph is divided into four quadrants: niche players, challengers, visionaries, and leaders. Gartner does not endorse any vendor, product, or service depicted in its research publications.
This is the fifth iteration of the Gartner 2017 Magic Quadrant for IGA report after the Gartner introduced the category in 2013, and it comes at an interesting time, as the market has hit a point of maturity where most can perform sufficiently in common use cases, and thus must look for new ways to differentiate their products.
At Solutions Review, we read the report, and pulled a few of what we considered the most important takeaways and key changes since the 2016 IGA MQ.
What is IGA?
According to the Gartner 2017 Magic Quadrant, IGA solutions are tools that “manage digital identity and access rights across multiple systems.” They accomplish this by aggregating and correlating identity and access rights data that is distributed throughout the IT landscape, in order to enhance control over user access. This aggregated data serves as the basis for what Gartner considers the core IGA functions:
- Identity Life Cycle and Entitlements Management
- Access Requests
- Workflow Orchestration
- Fulfillment via Automated Provisioning and Service Tickets
- Reporting and Analytics
- Role and Policy Management
- Auditing
Put simply, IGA is a set of processes used to manage identity and access controls across systems. IGA differs from IAM in that it allows organizations to not only define and enforce IAM policy but also connect IAM functions to meet audit and compliance requirements.
Movements on the Chart: Four Players Dominate ‘Leaders’ Quadrant, Challengers Close In
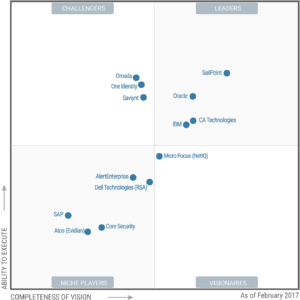 In 2016, the ‘leaders’ quadrant of Gartner’s graph featured just three vendors: Sailpoint, Oracle, and IBM. Flash forward to 2017, and those three vendors remain in the lead, with CA Technologies also entering the leader’s pack. Gartner praised CA for its highly-scalable solution and for improvements in ease of deployment, a significant pain point in the past.
In 2016, the ‘leaders’ quadrant of Gartner’s graph featured just three vendors: Sailpoint, Oracle, and IBM. Flash forward to 2017, and those three vendors remain in the lead, with CA Technologies also entering the leader’s pack. Gartner praised CA for its highly-scalable solution and for improvements in ease of deployment, a significant pain point in the past.
Just three vendors, Omada, One Identity, and Saviynt, remain in Gartner’s challenger’s quadrant, but all three have edged towards the leader’s quadrant, largely due to increased performance in “completeness of vision.” Gartner says that vendors in the challenger’s quadrant relatively strong set of governance and administration features,” and often net major clients, yet lack the “feature completeness, scale of deployment or vision for IGA that Leaders have.”
Canadian Hitachi ID Systems was dropped from this year’s report due to an increased minimum revenue inclusion criterion (vendors must now have roughly 1% market share by revenue to be included in Gartner’s report). Gartner also listed several “notable” IGA vendors that did not meet inclusion criteria for the report, including Avatier, Beta Systems, and ForgeRock, among others.
Widget not in any sidebars
A ‘Race To The Cloud’
As noted above, most IGA products have now matured to the point where they can fulfill all of the most common use cases, leading to what Gartner calls a “significant change phase,” as vendors rush to differentiate their products. Many vendors are now looking to the cloud as a key differentiator, and are building out cloud-delivered IGA or adding SaaS connectors to their on-premise software.
Gartner expects cloud-delivered IGA to evolve rapidly and significantly in the near future, but cautions CIOs and IT leaders to remain aware of the functional differences and trade-offs between traditional, on-premise IGA and IGA delivered as-a-service.
Analytics Adoption Still on the Rise
As more and more organizations come to the conclusion that traditional access certification methods are “inexact, labor-intensive, error-prone and insufficient to properly address inherent risks,” Gartner predicts a sharp rise in the use of analytics for “advanced risk analysis, fine-grained SOD analysis across the spectrum of corporate business systems with complex authorization models.” as well as decision support for approvals and certifications.
As the adoption and quality of analytics increases rapidly, Gartner predicts that mature organizations will increasingly apply analytics to help in the definition of identity management policies.
UEBA Integration Increases
One interesting emerging trend that Gartner noted among innovative vendors is the increased integration of user and entity behavior analytics (UEBA) capabilities, which allow for more intelligent real-time detection and response capabilities. According to Gartner, several vendors have had this capability on their product roadmaps “for years,” while others, such as Core Security, are already delivering UEBA integrations.
The Gartner 2017 Magic Quadrant attributes the focus on increased incident detection and response capabilities to the heightened attention given to insider threats in recent years.
(Editor’s Notes: In 2018 insider threats continue to plague the worst fears of enterprises and for good reason. Without the permissions controls and monitoring that come with Identity Governance and Administration solution, your enterprise could easily become a victim of its own access policies. Now is the time to evaluate your permissions policies, provisioning tools, and offboarding to ensure that security and regulatory compliance needs are being met.)




















