MDM and a Global Workforce: Creating Innovative Solutions for Better Security
 The following article was contributed by Bo Engelbrechtsen Ekkelund, Marketing Manager at Excitor, who brings over 10 years of experience in the IT industry. Excitor is the company behind DME (Dynamic Mobile Exchange), a software solution that enables companies and organizations to deploy, use, manage and control mobile services and all company mobile devices easily and effectively without compromising security and who recently was awarded a Highly Commended Award for DLP Solutions at SC (Secure Computing) Magazine Awards Europe 2013. The article highlights the impact mobile devices and BYOD programs are having on the enterprise and how DME goes beyond traditional Mobile Device Management (MDM) solutions in managing devices and protecting enterprise data and information.
The following article was contributed by Bo Engelbrechtsen Ekkelund, Marketing Manager at Excitor, who brings over 10 years of experience in the IT industry. Excitor is the company behind DME (Dynamic Mobile Exchange), a software solution that enables companies and organizations to deploy, use, manage and control mobile services and all company mobile devices easily and effectively without compromising security and who recently was awarded a Highly Commended Award for DLP Solutions at SC (Secure Computing) Magazine Awards Europe 2013. The article highlights the impact mobile devices and BYOD programs are having on the enterprise and how DME goes beyond traditional Mobile Device Management (MDM) solutions in managing devices and protecting enterprise data and information.
The proliferation of mobile devices among employees around the world is cause for celebration and concern. Smartphones and tablets gives access to rich content, breaking news, social media and world events. But security risks abound, with hackers and cyber thieves seeking to acquire sensitive corporate and client data, personal information and other confidential materials. In this situation, one where companies have offices throughout North America, Europe, Asia and the Pacific, the use of mobile device management (MDM) is not an adequate solution to the threats tens of millions of workers will face. And, while MDM has many merits and continues to be an option used by many public and private organizations, there are more innovative – and effective – ways to safeguard important content and protect businesses, suppliers, and individual administrators and salespeople from security violations and data loss.
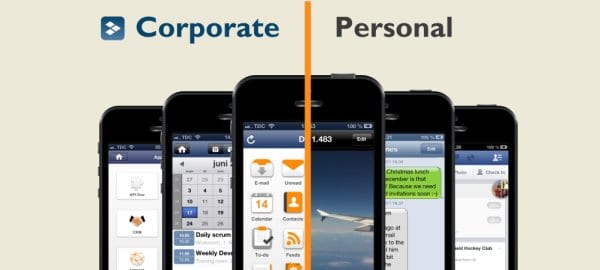
In this situation, where Bring Your Own Device (BYOD) is commonplace, we need to recognize that executives and their respective employees will – they already do – use their phones and tablets for both professional duties and recreational activities. Rather than treating these devices as a problem or forbidding their use entirely, companies should embrace this new era of technology – provided there is a series of significant upgrades involving MDM. (DME or Dynamic Mobile Exchange is an ideal solution for this challenge, as it enables an IT department – particularly one as large as the kind associated with a global corporation – to allow salespeople, HR personnel and other employees to conduct business securely with their work email addresses, calendars, contacts, news feeds, HTML5 applications and relevant intranets.)
It is important to note that what DME has to offer goes way beyond classic MDM. Using a secure corporate container, DME also has another key component, which is known as DME AppBox, this feature enables companies to deploy their own corporate AppStores, where each app is accessed securely using DME Appbox’s own secure browser. That degree of security and convenience is itself a significant innovation, where applications often drive the sales of mobile devices versus the opposite. And that benefit is yet another reason for the necessity – and effectiveness – of DME.
Bear in mind that global companies have legitimate concerns that these devices will cause problems for IT professionals; and there are fears aplenty about data leakage, creating the impression that any one of these items – from the proliferation of the iPad to the global popularity of Android smartphones – is the principal problem to maintaining security. This interpretation has merit, based on a study commissioned and published, respectively, by Cisco Systems and Syracuse University.
According to the report, 70 percent of IT professionals believe the use of unauthorized programs resulted in as many as half of their companies’ data loss incidents. Personal email is the most commonly used unauthorized application, followed by online banking, online bill paying, online shopping, and instant messaging. In addition, 46 percent of employees admit to transferring files between work and personal computers when working from home. Which returns us to the point that MDM, while worthy of some praise, is still not enough to overcome these challenges or assuage specific concerns about security. Not in the era of international communications. These concerns are diverse, ranging from worries about malicious applications to compromised security to the uploading of client data to personal devices, as well as anxieties about the physical theft of the devices themselves. For example: at least a third of most major organizations use MDM to monitor, manage and support the devices their employees use. Coupled with a poor definition of BYOD policies at these places (along with ad hoc rules governing security), and the problems are more apparent: MDM is an insufficient resource to protect information, prevent data loss and address the issues – and opportunities – of the BYOD era.
Please note: these statements are not an attack against MDM; but public and private organization– deservedly – want effective security and data loss controls. And, requiring sudden changes in behavior where users must always remember or reset complex passwords, is neither nor practical nor acceptable. All of which presents another problem when workers want to send a text message, access social media and balance their interests involving privacy and safety. IT departments must reconcile these demands with the need for protecting essential information.
At the same time, mobile applications represent another set of challenges. Sites like Facebook, Twitter, Dropbox and Evernote, as well as various news-related programs, may seek to directly or indirectly access and share organizational data. That information can end up in the wrong hands, forcing IT departments to (futilely) attempt to disable these applications or “blacklist” them as a way to prevent data loss. These tactics are not a realistic solution to an environment where there are over 1,000,000 applications available, collectively, from Apple (and their App Store) and the Android Marketplace.
For major companies, MDM requires a more robust – and flexible – solution than conventional remedies. In this environment, where there are so many mobile device users, there is an added need to not inconvenience these individuals. Offering the means to stop hackers, thieves and other cyber criminals is, thus, essential. With the right tools in place, we can all move beyond MDM to enjoy renewed protection and enhanced productivity. These benefits accrue to everyone, giving us cause for to welcome the ongoing transformation in the field of global communications.



















