Four Key Takeaways From Gartner’s 2016 Magic Quadrant for Identity Governance and Administration (IGA)
 Analyst house Gartner, Inc. has released the latest iteration of its annual Identity Governance and Administration (IGA) Magic Quadrant (MQ) report.
Analyst house Gartner, Inc. has released the latest iteration of its annual Identity Governance and Administration (IGA) Magic Quadrant (MQ) report.
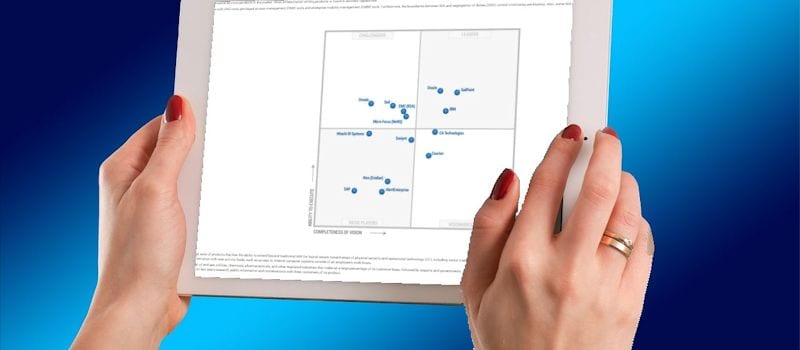
In the 2016 MQ for IGA Gartner evaluates the strengths and weaknesses of 15 vendors that it considers most significant in the IGA market, and provides readers with a graph (the Magic Quadrant) plotting the vendors based on their ability to execute and their completeness of vision. That graph is divided into four quadrants: niche players, challengers, visionaries, and leaders. Gartner does not endorse any vendor, product, or service depicted in its research publications.
This is the fourth iteration of the IGA MQ report since Gartner introduced the category in 2013, and it comes at a turbulent time—the IGA market is entering what Gartner calls “an early mainstream phase” after being thrust into the business world’s consciousness by a series of highly public data breaches that have sent CIOs scrambling to find new ways to secure their information.
[ How to Use Gartner's Magic Quadrants and Critical Capabilities Reports for Identity Management ]
At Solutions Review, we read the 28-page report, available to Gartner subscribers here, and pulled a few of the most important takeaways. But before we get to the meat and potatoes, let’s get Gartner’s definition of IGA out of the way.
What is IGA?
According to Gartner, IGA solutions are tools that “manage identity and access life cycles across multiple systems in a heterogeneous environment.” They accomplish this by aggregating and correlating identity and access rights data that is distributed throughout the IT landscape to enhance control over user access. This aggregated data serves as the basis for core IGA functions.
According to Gartner, core IGA functions include:
- Identity Life Cycle Management
- Access Requests
- Workflow Orchestration
- Role and Policy Management
- Auditing
- Access Certification
- Fulfillment via Automated Provisioning and Service Tickets
- Reporting and Analytics
- Password Management
The 2016 IGA MQ report rates vendors on the ability to deliver those core capabilities “in a product specifically tailored and sold to manage access request life cycles.”
Put simply, IGA is a set of processes used to manage identity and access controls across systems. IGA differs from IAM in that it allows organizations to not only define and enforce IAM policy but also connect IAM functions to meet audit and compliance requirements.
User Experience is Forefront
Over the course of the past few years, user experience has become a forefront selection criteria for IGA solutions. Employers are realizing that their users are less likely to properly use a cumbersome, convoluted IGA system, which can create a whole new host of security problems. Due to
Due to these changing attitudes, Gartner’s analysts note that most vendors have either “significantly re-engineered their IGA business user interfaces” or are currently doing so. “Those few vendors that have not yet caught up have indicated this to be on their roadmap”, says Gartner.
Pressure Mounts for Consumer Identity and Access Management (CIAM)
As more and more identity stores and directories are mitigated to the cloud, pressure is mounting for IGA tools table to manage vast amounts of consumer identities, says Gartner.
But consumer identity management “is different”, says Gartner—the requirements for a good CIAM aren’t quite the same as those for IGA tools used for managing employee and contractor identities.
For example, unlike traditional IAM, customer focused solutions need to be able to scale dramatically to handle increased traffic. A traditional IAM solution may be able to support thousands of employees, but will unlikely be able to scale to meet the elastic demands of a customer-facing website.
Gartner’s analysts have observed some IGA vendors reacting to this pressure by “aggressively discounting for external identities such as consumers, while others are offering special editions of their offering for external identity management.” In any case, CIAM isn’t going away, and we can expect many of the bigger players in the IGA market to expand their focus on managing consumer identity in the coming months and years.
Analytics Adoption on the Rise
As more and more organizations come to the conclusion that traditional access certification methods are “inexact, labor-intensive, error-prone and insufficient to properly address inherent risks,” Gartner predicts a sharp rise in the use of analytics for “advanced risk analysis, fine-grained SOD analysis across the spectrum of corporate business systems with complex authorization models.” as well as decision support for approvals and certifications.
Gartner predicts that by 2018, analytics, machine learning and policies will replace more than 50% of manual access certification and request approval tasks, up from less than 2%.
Integration is the Name of the Game
One interesting emerging trend that Gartner noted among innovative vendors is the increased integration of IGA solutions with related tools, such as Data Access Governance (DAG), privileged access management (PAM), and enterprise mobility management (EMM) tools.
DAG integration has been particularly steady, due to the close relationship between application and data access, says Gartner, and several companies such as SailPoint, Courion, Dell, Micro Focus, and Saviynt currently offer both types of products and could benefit from “further integration and upsell opportunities,” says Gartner.
Gartner predicts that by 2020, 50% of enterprises with identity governance and administration (IGA) deployments will have invested in data access governance (DAG) for tighter data access control, up from less than 10% today.
Integration between IGA products and PAM products is also on the rise, with growth driven by interest from clients and competition from PAM/PIM vendors approaching IGA territory.
Widget not in any sidebars


















