Building the Privileged Identity Management Business Case for IAM – Xceedium
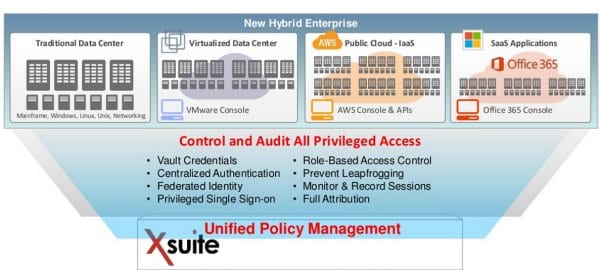
This recent Xceedium presentation outlines the importance of focusing on the privileged identity and user when address Identity and Access Management initiatives. The idea of privileged users strikes at the heart of internal threats to corporate data, information and loss of revenue. The presentation sites a Forrester statistic that states insiders were the top source of breaches in the last 12 months and that some say insider breaches and threats are more likely to cause more damage to an organization than external attacks. Check out this presentation to understand more about the risks of internal threats from privileged users and how to build a business case for privileged identity Management an privileged access control.



















