Five Reasons Traditional IAM Can’t Handle the Internet of Things
 It may sound futuristic to some, but the Internet of Things (IoT), that nebulous net of connected everything, is here at last, and it’s only getting bigger— the global IoT market is expected to grow to $7.1 trillion by 2020, compared to $1.9 trillion in 2013, and companies all over the globe are scrambling to meet the opportunity.
It may sound futuristic to some, but the Internet of Things (IoT), that nebulous net of connected everything, is here at last, and it’s only getting bigger— the global IoT market is expected to grow to $7.1 trillion by 2020, compared to $1.9 trillion in 2013, and companies all over the globe are scrambling to meet the opportunity.
Connected cars, homes, tools, factories, and even toys are all coming to market—what was once a Jetsons-like SciFi daydream is now a reality, and for many security pros, it’s a harsh reality.
As we adopt connected devices and embrace their ability to change our world for the better we may also be unwittingly inviting untold security vulnerabilities into our daily lives.
As often happens with fast-moving emerging markets, IoT solution providers are under huge pressure to build and launch solutions quickly. Unfortunately for the consumer, that rush to market can mean that important features such as security, access governance and privacy management get overlooked, resulting in massive vulnerabilities like hackable cars and homes.
In fact, enterprise tech research and analysis firm Gartner, Inc. predicts that by 2020, more than 25 percent of identified attacks in enterprises will involve IoT, and yet, the same study predicts that IoT will account for less than 10 percent of IT security budgets.
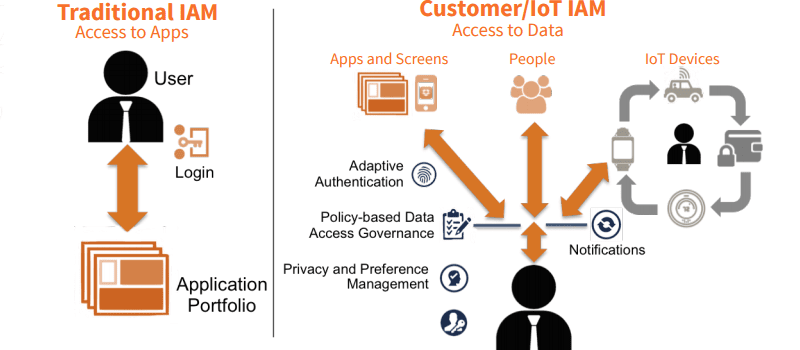
One particular problem area for IoT security is Identity Management. In many ways, the Internet of Things is fueled by the identities of things to enable connections between people, devices, and apps, all of which require Identity and Access Management (IAM).
Indeed, managing identities and controlling access to this valuable information is a critical step in securing the Internet of Things (IoT), but legacy identity and access management (IAM) systems cannot handle the extreme scale and complexity that the IoT brings to the enterprise.
The Identity of Things requires a new class of IAM system. The best practice for managing identity in the Internet of Things is to employ a next-generation IoT IAM platform. But what exactly does next-gen IoT IAM entail? And how does it succeed where traditional, workforce IAM fails?
In their new whitepaper, Overview of Identity Management for the Internet of Things, the folks at UnboundID layout the basics of IoT vulnerabilities and the identity management capabilities that can remove the barriers to IoT adoption.
Additionally, UnboundID identifies five key requirements that differentiate next-gen IoT IAM solutions from traditional IAM—security best practices, adaptive authentication, privacy and preference management, policy-based data access governance, and high volume scale—and offer case studies and diagrams to back up their findings. To learn more, get the full report here.
Interested in learning more about identity management? Check out these additional resources:






















