2014 State of Endpoint Risk Study Highlights Increasing Malware Threats

The report points out the challenges that IT professionals face in securing company networks because of the rapid increase of mobile platforms and public cloud resources. In the past 12 months, 65 percent reported enduring an Advanced Persistent Threat (APT)/a targeted attack. One of the main causes of the APT attacks are spear phishing emails sent to employees. According to the report, the top three applications with the highest IT risk were: Adobe (60 percent), Google Docs (50 percent), and Microsoft OS/applications (37 percent).
Additionally, 44 percent say that cloud computing infrastructure and providers like Dropbox represent major security concerns. Despite the potential risk for more security threats, only 44 percent are expecting their IT security budgets to increase in 2014. For 2014, the technologies that IT professionals expect to invest in are: application control, “big data analytics,” data-loss prevention, device control, and MDM.
Additional highlights from the 2014 State of Endpoint Risk study
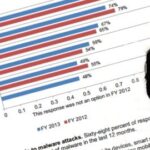
* 41 percent say they experience more than 50 malware attacks per month.
* In the past two years, the majority of respondents say endpoint security is a priority for their company’s overall IT security plan.
* More than ½ of respondents indicate that their company has a BYOD policy that allows employees use their personal mobile devices for work-related purposes.
Larry Ponemon, Ph.D., is the chairman and founder of the Ponemon Institute. Ponemon says that enterprises have lost customer and employee data from the evolution of cyber security risks over the past five years. An example of the increase in cyber threats is the recent customer information breach at mega-store discount retailer Target. “We’ve seen the threat landscape fundamentally change over the last five years. Trending data shows increasing concern, year over year, over the explosion of mobile devices on the network. It’s now IT’s greatest risk. And unfortunately, 45% of our respondents report no effort in place to secure them,” says Ponemon.
To read the Ponemon Institute’s entire “2014 State of Endpoint Risk” study click here:



