All Day DevOps: How to Secure Docker Containers


Cloud computing events are invaluable for learning the latest tips and tricks of the space. Unfortunately, many of us can’t attend events due to location or costs. To alleviate this struggle, All Day DevOps was created. This online conference takes place of 24 hours with 112 sessions for free! Each session led by industry professionals in a variety of areas.
To help kick this event off, we connected with Jose Manuel Ortega to learn more about his upcoming speech, Common Vulnerabilities & Exposures in Docker Containers. Jose has technical knowledge across the IT space, but specializing in application security. Read more about Jose at the bottom of this post.
Be sure to check out our preview of Daniel Baker’s session as well.
Common Vulnerabilities and Exposures in Docker Containers
In this talk, I will start explaining Docker images as composed of several immutable layers. The Docker build process follows a manifest called Dockerfile that includes relevant security information that you can scan and evaluate including the base images, exposed ports, environment variables, entrypoint script and external installed binaries.
In a secure pipeline, Docker image scanning should be a mandatory step of your CI/CD process and any image should be scanned and approved before entering running state in production.
The container image scanning process typically includes:
- Checking the software packages, binaries, libraries, operative system files, etc. against one or more well-known vulnerabilities in databases. Some Docker scanning tools have a repository containing the scanning results for common Docker images that can be used as a cache to speed up the process.
- Analyzing the Dockerfile and image metadata to detect security sensitive configurations like running as privileged (root) user, exposing insecure ports, using based images tagged with “latest” rather than specific versions for full traceability, etc.
- User-defined policies, or any set of requirements that you want to check for every image, like software packages blacklists, base images whitelists.
The CVE(Common Vulnerabilities and Exposures) is a database of known information security vulnerabilities. We can find CVEs that are directly related to Docker security incidents or issues. Vulnerabilities in the scan report are assigned a severity of high, medium, or low. Severity is based on the Common Vulnerability Scoring System (CVSS) score assigned to the CVE.
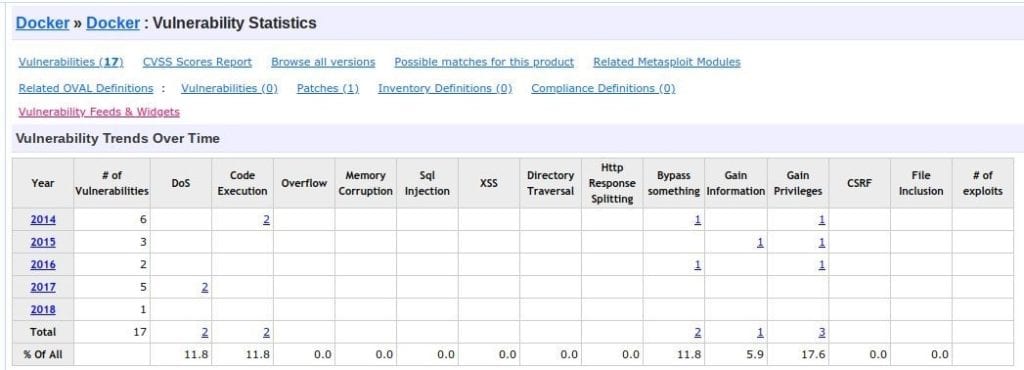
For obtaining the criticality level of a vulnerability also we can use some metrics like access vector, network, access complexity, authentication, and confidentiality impact:
- Access vector: This metric reflects how the vulnerability is exploited. The more remote an attacker can be to attack a host, the greater the vulnerability score.
- This metric measures the impact to the integrity of a successfully exploited vulnerability. Integrity refers to the trustworthiness and guaranteed veracity of information. Increased integrity impact increases the vulnerability score.
- Access Complexity: This metric measures the complexity of the attack required to exploit the vulnerability once an attacker has gained access to the target system. For example, consider a buffer overflow in an Internet service: once the target system is located, the attacker can launch an exploit at will.
- Authentication: This metric measures the number of times an attacker must authenticate to a target in order to exploit a vulnerability. This metric does not gauge the strength or complexity of the authentication process, only that an attacker is required to provide credentials before an exploit may occur.
- Confidentiality Impact: This metric measures the impact on confidentiality of a successfully exploited vulnerability. Confidentiality refers to limiting information access and disclosure to only authorized users, as well as preventing access by, or disclosure to, unauthorized ones. Increased confidentiality impact increases the vulnerability score.
We will review the main container threats. Due to containers will always share the host kernel. Therefore, any vulnerability in the kernel interface can be exploited by the container to harm the host; unless you use seccomp or apparmor for limit syscalls between the container and the host.
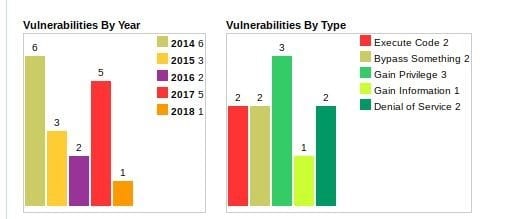
Examples of container attacks
Dirty Cow (CVE-2016-5195). Dirty Cow is kernel vulnerability that enables any unprivileged existing user to increase its privilege to root.
GHOST (CVE-2015-0235). Ghost is a buffer overflow bug affecting the gethostbyname() and gethostbyname2() function calls in the glibc library. This vulnerability allows a remote attacker that is able to make an application call to either of these functions to execute arbitrary code.
Other container attacks include OpenSSL heap corruption caused by malformed key header and a crash caused by the presence of a specific extension and vulnerabilities like the glibc stack-based buffer overflow, giving hackers control through the use of man-in-the-middle attacks.
Container image scanning open-source tools
One of the main steps of the CI (Continuous Integration) pipeline involves building the container images that will be pulled and executed in our environment. Therefore, whether you are building Docker images from your own code or but also when using unmodified third-party images, it’s important to identify and find any known vulnerabilities that may be present in those images. This process is known as container image scanning.
There are several Docker image scanning tools available, and some of the most popular include:
- Docker Security Scanning is a service that scans container images to see if any of their components contain known security vulnerabilities. Scan for known vulnerabilities, based on a continuously updated feed based on multiple sources.
- Anchore Engine is an open source image scanning tool. Provides a centralized service for inspection, analysis and applies user-defined acceptance policies to allow automated validation and certification of container images.
- CoreOS/Clair is an open source project for the static analysis of vulnerabilities in application containers.
- io: Agent-less Linux vulnerability scanner based on information from NVD, OVAL, etc. It has some container image support, although is not a container specific tool.
- Dagda is an open source tool developed in Python to perform static analysis of known vulnerabilities in Docker images/containers. It also helps you to monitor running Docker containers for detecting anomalous activities. To do so, it retrieves information about the software installed in your Docker image, such as the OS packages, the dependencies, modules, etc. and matches it against a vulnerability database.
These tools will compare the contents of a container, by inspecting the binary packages in that container against the Common Vulnerabilities and Exposures (CVE) database, which offers a listing of known security vulnerabilities of the most commonly-used open source and proprietary software packages.
Anchore is a set of tools that provide visibility, transparency, and control of your container environment. With anchore, users can analyze, inspect, perform security scans, and apply custom policies to container images within a CI/CD build system. Also can be integrated directly into your container environment.
Anchore Navigator provides a free service for deep inspection of public Docker images. You can also explore their rich repository of already-dissected images for full visibility of its content, build process, and discovered CVE threats together with a link to the complete issue description and known fixes.
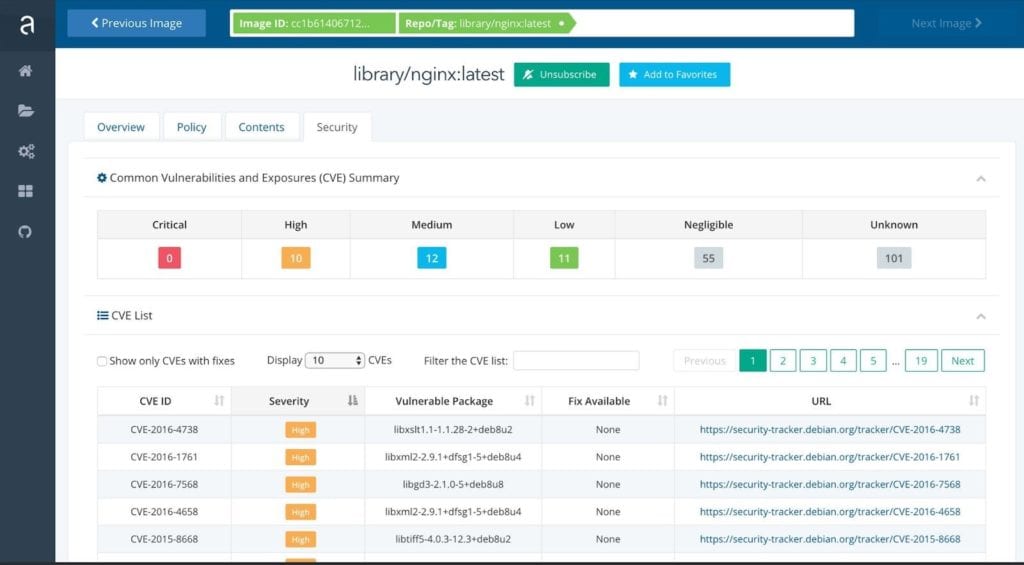
Also, we will review some techniques like composition analysis that allow us to check library and supporting code against the CVE (Common Vulnerabilities and Exposures) database to determine whether you are using vulnerable code.
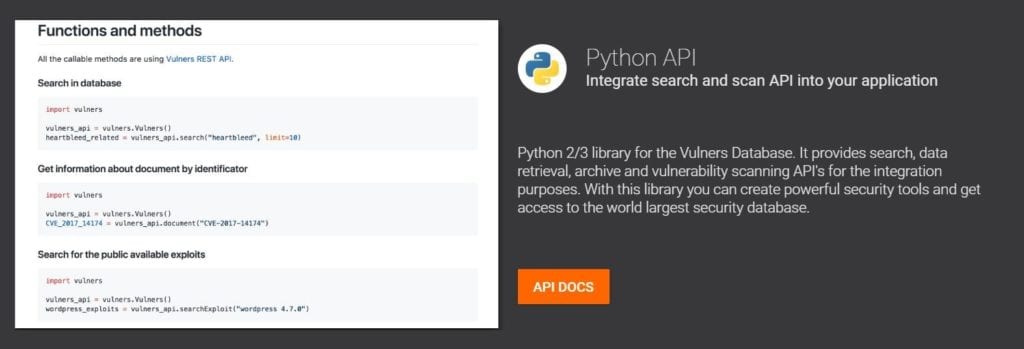
We will review other tools like Vulners Database . It provides search, data retrieval, archive, and vulnerability scanning API’s for the integration purposes. With this library, you can create powerful security tools and get access to the world largest security database. It provides python API for getting information about CVE by identifier. You cabn also search for public availa exploits and get vulnerabilities and exploits by software name and version.
From Jose Manuel Ortega:
My career has been focused from the beginning to specialize in application security. My strengths live on at the technical level by the type of training that I have received in recent years and the projects where I have worked. In recent years, I’m interested in mobile applications development, especially on android platform and integrating with other languages like scala or python. At this moment I am working as business logic developer and my functions in the project are analysis, coding, and testing. With the help of software architecture developer, also performance roles in the presentation and backend layer.




















