Fuzzy Logic: Bridging the Gap Between AI and Real Life Cyber Attacks
Fuzzy Logic: Bridging the Gap Between AI and Real Life Cyber Attacks
By Rami Cohen, VP R&D of empow
The new generation of cybersecurity products in orchestration, mitigation, and response depends more and more on Machine Learning (ML) and Artificial Intelligence (AI). This is the right way to go because the immense volume of cyber-attacks overwhelms security analysts (often an understaffed team to begin with) and AI can usefully filter out the noise and make security tools and cybersecurity operations more efficient.
Widget not in any sidebars
But AI comes in many forms, that represent various approaches for problem-solving. How do we fit the right AI to the right problem?
In certain scenarios, for example when there are a variety of demand settings, lots of features or models, a lot of missing and vague pieces of information, and when we need a deeper understanding and intuition to reach the right conclusion, AI can only tell us so much.
Take, for example, a picture constructed out of thousands of pixels. ML can work its automation magic and decide that the photo of a dog is indeed a dog. The typical ML models work great in this case, since we don’t need to know, nor do we care, how the conclusion was reached.
But what if one of the computers in our network is behaving strangely? It has become more challenging to adapt and recognize patterns when someone tries to change his behavioral features all the time, like in the case of cyber-attacks. In these cases, ML-based Network Traffic Analysis (NTA), or User Behavioral Analytics (UEBA), tools identify an anomaly but can’t get to the next step of identifying what caused the behavior. Was it a brute force attack? A data leak? Compromised host or identity theft? Something else?
There may be a number of features within each scenario, a combination of which created the anomaly, but the level of understanding of which one deviated, as well as the ability to influence the decision-making process, is very limited.
Enter Fuzzy Logic. Fuzzy Logic uses mathematics to represent vague (or “fuzzy”) and imprecise information and reach decisions. Fuzzy Logic was invented in 1965 by Lotfi Zadeh, a UC Berkeley mathematician who concluded that computational logic was not the best logic to use when manipulating data representing subjective human ideas.
Fuzzy logic approaches computing through the lens of “degrees of truth” rather than the usual “true or false” (1 or 0) Boolean logic. We can say it’s closer to “human” logic than other computational approaches.
Today Fuzzy Logic algorithms are almost everywhere, from the antiskid feature in your car to chatbots, weather forecast, and stock trading.
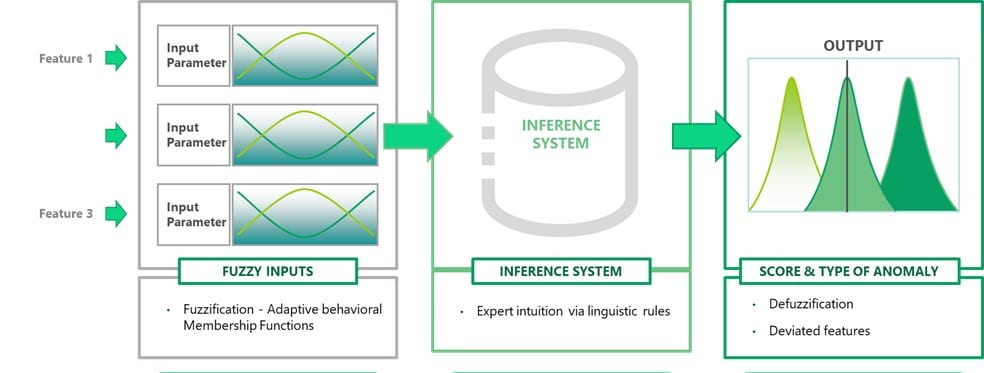
If we go back to our misbehaving computer, Fuzzy Logic allows the algorithm to receive human expert inputs (intuition inputs in a linguistics representation) and weigh them as part of the inference process before making a decision. In this way, it can tell us not only THAT the computer is displaying anomalous behavior, but it can also tell us how that was decided, which features were involved, and what type of anomaly behavior it is exactly.
The ability to inject human intuition in simple linguistic representation allows us to create new anomaly detection engines faster than with other AI approaches.
Here’s a diagram that explains the Fuzzy Logic Process:
Albert Einstein said “So far as the laws of mathematics refer to reality, they are not certain. And so far as they are certain, they do not refer to reality.” Using Fuzzy Logic in cybersecurity can help bridge the gap between tools like ML and our reality, helping to better protect our networks from very real cyber-attacks.
Thanks to Rami Cohen, VP of R&D at empow for his time and expertise. For more information, check out our SIEM Buyer’s Guide.
Widget not in any sidebars



















