Most Businesses Rely on Outdated Security Tech, Survey Says

APRIL 20, 2015 — A majority of Enterprises are relying on outdated technology for network access control (NAC), according to survey results released by encryption and identity-based security solutions vendor Cryptzone this morning at RSA Conference 2015.
The survey was conducted by Cryptzone and third-party research organization TechValidate to assess enterprise NAC policies and security solutions, and particularly how enterprises are addressing “today’s environments, given the proliferation of cyber crimes and growing concerns over insider threats”, according to a press release.
The report’s results highlight a widespread use of outdated solutions and approaches to cyber security. Specifically, Cryptzone says the report points out a “lack of advanced solutions to limit the carte blanche access granted to employees and third parties under older network security models.”
According to the survey’s results, the majority of businesses still rely on decades old virtual private network (VPN) technology for controlling network access.
“It’s remarkable that many organizations are still utilizing network security technologies developed in the nineties – a time when the Internet was still in its infancy,” said Kurt Mueffelmann, president and CEO for Cryptzone. “The cyber attacks we have seen over the last few years, have demonstrated that it’s far too easy for hackers to steal user credentials, and then use those credentials to traverse the enterprise network in search of the most valuable data.”
Survey results say that, while hacking is perceived as the largest threat to security, most breaches result from user mistakes or accidents. Also, recent research from Sailpoint tells us that disgruntled employees may be willing to sell privileged access info, which could have disastrous results for a business.
“Organizations must stop giving out the keys to the kingdom when it comes to privileged users, third party, and employee access,” says Mr. Mueffelmann.
During the RSA Conference, Cryptzone will reveal its newest product, AppGate® Secure Access, “an integrated security gateway that provides a secure, encrypted, service-specific tunnel between user and application or resource.”
Those of you at RSA Conference can learn more by talking to Cryptzone at booth #S224; everyone else can check out the survey results below:
VPNs still Dominant Form of Network Access Control
- 91% of respondents shared that VPNs are still the main form of security for controlling network access.
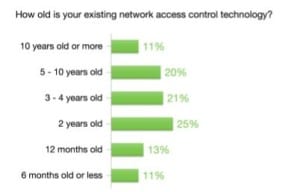
- A majority (51%) noted that their access control technology was greater than three years old, and 11% said it was more than 10 years old.
- Host IPS, next-gen firewalls, identity management solutions and vulnerability assessment all followed the two leading solutions but were only being used by between 24-30% of the organizations for the purpose of access control.
- Exactly half said that their network access/firewall rules were static.
- Only 21% of companies rely on attribute-based controls to secure access; most rely on authentication (93%) and session authorization (46%)
Perceived vs. Actual Risk
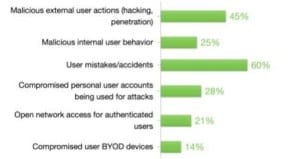
- The survey also revealed that malicious external user actions (hacking) were perceived as the greatest security risk to an organization (66%), followed closely by user mistakes/accidents (56%).
- But upon reviewing the threats that had caused the most actual harm or damage to organizations in the last 12 months, 61% noted user mistakes/accidents and only 46% noted malicious external user actions.
- While outsiders often are the ones attacking an organization, they must find a point of vulnerability in order to actually create a breach and cause damage.
Who Owns Policy Control
- 48% of respondents concluded that the main controllers of policy were their IT departments.
- 36% said information security.
- 12% said compliance or risk management.
- Only 3% identified business owners as policy control managers.
- More than half of companies (52%) have not reviewed their access policies in over a year.
- 42% of companies can’t or don’t automatically enforce security policies.
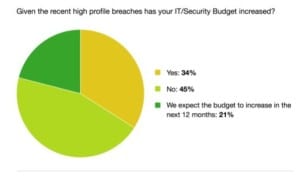
- Surprisingly, 45% of respondents said their security budget had not increased, despite recent high-profile breaches. An additional 21% said it had not increased, but they expected it would in the next 12 months.
For more Identity and Access Management information, check out our Free 2015 IAM solutions Buyer’s Guide