Fiberlink MaaS360 (IBM) Addresses Malware with Mobile Threat Management (MTM)
 We recently featured Fiberlink’s (MaaS360 an IBM company) layered approach to mobile security. This layered approach attempts to touch on every aspect of mobile security from the device, to apps used and even the browsers utilized by end users. A recent post from Fiberlink/IBM highlights yet another aspect of mobile security and another level to Fiberlink’s layered approach that the enterprise should probably be aware of.
We recently featured Fiberlink’s (MaaS360 an IBM company) layered approach to mobile security. This layered approach attempts to touch on every aspect of mobile security from the device, to apps used and even the browsers utilized by end users. A recent post from Fiberlink/IBM highlights yet another aspect of mobile security and another level to Fiberlink’s layered approach that the enterprise should probably be aware of.
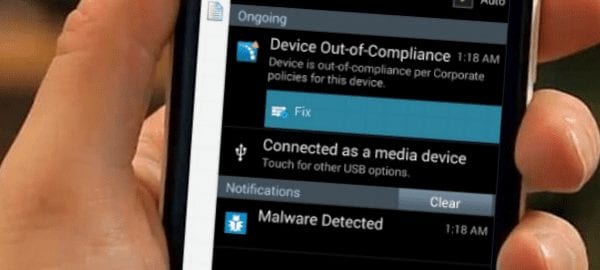
The company has recently released MaaS360 Mobile Threat Management (MTM) which looks to detect, analyze and re mediate malware issues around enterprise mobility and Mobile Device Management. They write, “IBM believes this is a vital part of complete enterprise mobility management and any responsible mobile initiative.” Malware has always been an issues and as the enterprise continues to deploy mobile devices or allow employees to bring their own (BYOD) malware issues will continue to grow. The blog written by Joshua Lambert, Senior Product Manager at IBM, reads “How much of a wake-up call do we need? These attacks threaten sensitive corporate data such as financials, credit card accounts, patient records, intellectual property and customer information. With the increasing threat to data on mobile devices, enterprise mobility management solutions are perfectly positioned to provide a central point of policy, security and productivity for businesses.”
So what is MaaS360 Mobile Threat Management (MTM) all about? Here is a quick run down of features and a link back to Fiberlink to learn more about what they have to offer.
* Detect apps with malware signatures from a constantly updated database;
* Alert both the user and administrator when malware is detected;
* Automatically restrict mobile app and device functionality based on detected risks and policy requirements;
* Immediately restrict access to corporate email, calendar, contacts, apps and content;
* Remediate in near real time based on an IT-configured compliance rules engine;
* Protect both Android and iOS devices.